Thinking Outside the Security Blog
Thinking Outside the Security Blog
Check back often for blog posts and news about cyber security and vulnerabilities.
The human aspect of Information Security
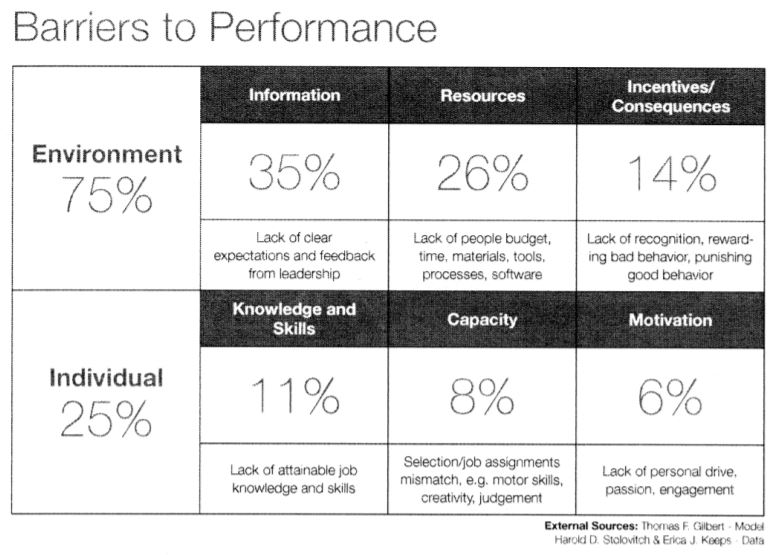
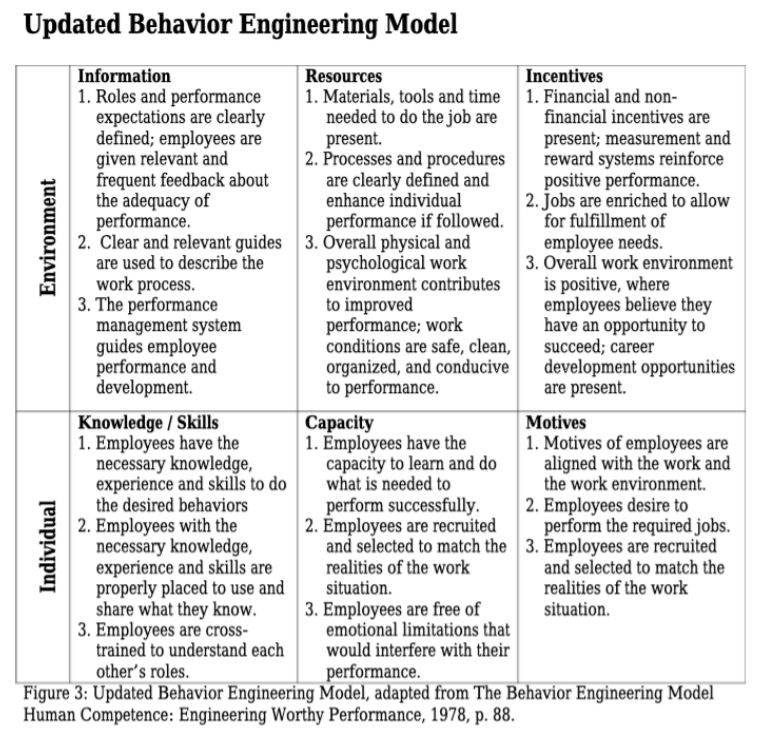
In Information Security, there is a saying, “people are the weakest link.” While there are certainly resources out there, how many are put into practice? How many of you still have to take those annual training courses?
There is one thing I want to make clear, I do not think people are the weakest link. It’s simply another aspect of Information Security that we need to address. When you hear an Information Security Professional state “well, people are stupid, they should understand this stuff.” The end-user is not the weakest link, that person is. You have not done enough to understand the problem and try different ways of doing things.
 This is the first in a series of blogs looking at the human aspect of Information Security. This blog will be a quick review of a book called Brain Rules by John Medina. I will only comment on 5 of the rules.
This is the first in a series of blogs looking at the human aspect of Information Security. This blog will be a quick review of a book called Brain Rules by John Medina. I will only comment on 5 of the rules.
The first rule I will discuss is Survival. Our brains evolved to solve problems and work together in groups. In Information Security, there is a silo or “secret squirrel” nature for some reason. The truth is that we are all in this together and need as much support as possible. Build your network of people and organizations to learn. For the learner, consider having a security challenge that encourages your employees to work together as a team. There could even be winners selected for prizes.
The second rule I will discuss is Wiring. Every brain is wired differently. For the learner, this could be implemented in by customizing the training. For example, an assessment test would be conducted to see what the learner's “weak” points are. The Learning Management System (LMS) would then create a course specifically tailored to them. Without this customization, the learner has to look through material they already understand, which then leads to boredom and they check out for the rest of the training.
The third rule I will discuss is Attention. We don’t pay attention to boring things. Outside of the Information Security org, how many people really think InfoSec is interesting? You need to think about making the training more fun…like gamification! Ok, so now you have training that has been turned into a game. Even when the subject is not boring, people’s attention tends to wander every 7-11 minutes. Most annual training is around 30 minutes. You’ve lost them at least 3 times! Usually, that is lost to “oh hey, I got a new email I need to read.” Think about setting aside a time (in staff meetings) where the learner can take the course undistracted. For those companies that have employees that CAN’T be taken away from their job, how about paying them during lunch or after work to take the training?
The fourth rule I will discuss is Memory. Lather, Rinse, Repeat. Repetition is one of the keys to memory. With annual training, there is no repetition. We need to be reminded much more often. There needs to be follow-up training to see what stuck. For those people that love metrics, companies can use the Kirkpatrick Model. Level 1 should be conducted right after the training, then the other levels can be conducted some time down the road.
The last rule I will discuss is Sensory Integration. The more you can evoke all the senses (sight, sound, taste, smell, and touch) in training the better. I am not sure how to integrate smell and taste into Information Security, but if you have any ideas, feel free to email me. To incorporate touch into the training, consider taking advantage of the touch screens in most of the devices we have now, instead of the “click next, click next.” To incorporate sounds in the training, you can use some context relative (each audience or culture may have common reactions to sounds) sounds. For example, you can use a crashing sound, or zapping (yes, I know zapping people for bad infused behavior is appealing….) to indicate an incorrect choice. Or perhaps a cheering sound when the learner made the right choice. Now for the most important sense, SIGHT. Sight trumps all other senses. You have heard of the phrase “A picture is worth a 1000 words.” There is truth to that. The brain reads every letter of this blog as a separate image. It seems easy, but the brain has had a LOT of practice. For training, STOP putting in slides that say “Do not click on URLs that blah blah blah.” Find ways to use impactful pictures to say the same thing.
Stay tuned for future blogs looking at the human aspect of Information Security.
Most Recent Posts ...
Posted on: 6/24/2021
Posted on: 5/20/2021
Posted on: 4/20/2021
Posted on: 2/1/2021
Search All Blog Posts
Blog Post Archives
- People Security - Behavior Engineering and Information Security
- People Security - Behavior Engineering and Information Security
- SolarWinds, cuz everyone else is...
- People Security - Behavior Engineering and Information Security
- The human aspect of Information Security